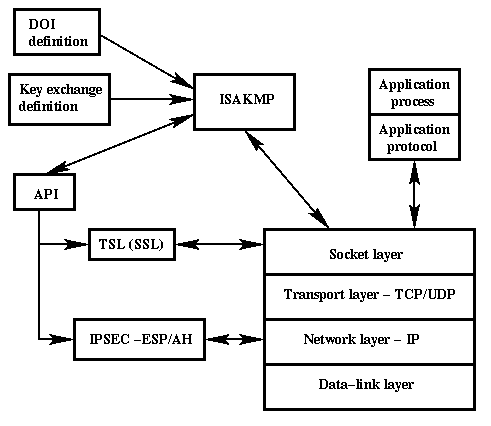
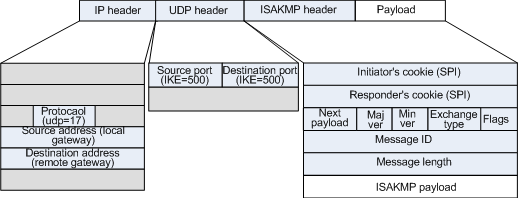
Isakmp
Also add info of additional Wireshark features. To set the terms of the ISAKMP negotiations you create an ISAKMP policy which includes the following.

Handbook Fortigate Fortios 6 0 0 Fortinet Documentation Library
There are many possible reasons why this could happen.
Isakmp. Reply 2 on. 10112 10111 MM_NO_STATE 1 0. Implementations MUST include send and receive capability for ISAKMP using the User Datagram Protocol UDP on port 500.
Crypto isakmp keykeystring hostname peer-hostnameSo the correct answer would be the following. Verify that the phase 1 policy is on both peers and ensure that all the attributes match. Phase 1 and Phase 2.
A show crypto isakmp sa command shows the ISAKMP SA to be in MM_NO_STATE. May 15 2020 033059 pm Thanks mimugmail your reply was insightful and raises specific OpenVPN question not related to this post so Ill give it some thought and maybe post a different question. ISAKMP is distinct from key exchange protocols in order to cleanly separate the details of security association management.
This article provides information about the log entry The peer is not responding to phase 1 ISAKMP requests when using the global VPN client GVC. Hash MD5 or SHA. Also add info of additional Wireshark features.
La négociation ISAKMP se compose de deux phases. Crypto isakmp client configuration group outlan-ras. UDP Port 500 has been assigned to ISAKMP by the Internet Assigned Numbers Authority IANA.
ISAKMPでは インターネット の セキュリティアソシエーション を IP パケットレベルで 確立 しているが 具体的な 鍵 交換方 法が 規定 され ていない ため 多く の鍵. In this article we would discuss that in detail. Phase 2 creates the tunnel that protects data.
ISAKMP is distinct from key exchange protocols in order to cleanly separate the details of security association management. In this article we would discuss. ISAKMP traffic normally goes over UDP port 500 unless NAT-T is used in which case UDP port 4500 is used.
ISAKMP uses UDP port 500 for communication between peers. Organizations are setting up Virtual Private Networks VPN also known as Intranets that will require one set of security functions for communications within the VPN and possibly many different security functions for communications outside the VPN to support geographically separate. ISAKMP traffic normally goes over UDP port 500 unless NAT-T is used in which case UDP port 4500 is used.
ISAKMP and Outbound NAT Rules. In ISAKMP SA and key management are separate from any key exchange protocols. Oakley provides perfect forward secrecy PFS for keys identity protection and authentication.
ISAKMP Internet Security Association et Key Management Protocol et IPSec sont essentiels à la construction et au chiffrement du tunnel VPN. Crypto isakmp policy 1000 encr 3des hash md5 authentication pre-share group 2 crypto isakmp keepalive 20 5 crypto isakmp nat keepalive 30. ISAKMP defines payloads for exchanging key generation and authentication data.
Authentication rsa-sig rsa-encr pre-share The. Wireshark The ISAKMP dissector is fully functional partially functional not existing. Example traffic XXX - Add example decoded traffic for this protocol here as plain text or Wireshark screenshot.
ISAKMP とは 認証 方法 と 暗号化 鍵の 交換方 法の フレームワーク の 一種 である. For Cisco platforms IKE is analogous to ISAKMP and the two terms are used. R1config crypto isakmp key cisco123 address 209165200227 R2config crypto isakmp key cisco123 address 209165200226.
The RFC you have referred to states that ISAKMP is an IPSEC protocol and it is trueJust that that new devices make use of IKE to setup VPN connnections. Such an instantiation is denoted as the. ISAKMP can be implemented over any transport protocol or over IP itself.
ISAKMP defines header and payload formats but needs an instantiation to a specific set of protocols. CCNA Security Chapter 8 Exam Answers More Questions. ISAKMP separates negotiation into two phases.
An authentication method to ensure the identity of the peers. ISAKMP protocol to establish a framework for authentication and key exchange Oakley describes a series of key exchanges and services SKEME key exchange technique that provides anonymity repudiabilityand key refreshment. This also means that main mode has failed.
So in a sense ISAKMP is an abstract protocol it provides a framework for authentication and key management and supports many actual key exchange protocols eg IKE. 解決方法が見つかりました isakmpはikeの一部ですikeにはisakmpskemeおよびoakleyがありますikeは共有セキュリティポリシーと認証済みキーを確立しますisakmpは鍵交換のメカニズムを指定するプロトコルです 私にとっては混乱はcisco iosでは同じものを指すためにisakmp. IPsec Overview TheASAusesIPsecforLAN-to-LANVPNconnectionsandprovidestheoptionofusingIPsecfor client-to-LANVPNconnectionsInIPsecterminologyapeer isaremote.
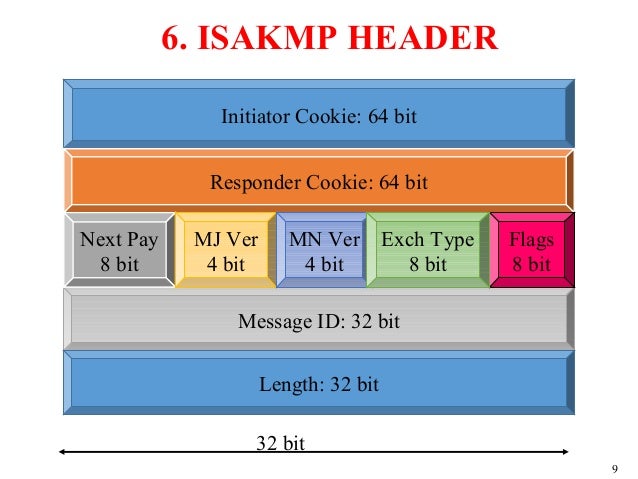
These formats provide a consistent framework for transferring key and authentication data independent of the key generation technique encryption algorithm and authentication mechanism. Whatever the current state is. Diffie-Hellman Group 1 or 2.
Please login or Register to submit your answer. IPsec ISAKMPInternet 安全连接和密钥管理协议ISAKMPInternet Security Association and Key Management Protocol Interne 安全连接和密钥管理协议ISAKMP是 IPsec 体系结构中的一种主要协议它结合加密安全的概念密钥管理和安全连接来建立政府商家和因特网上的私有通信所需. Dst src state conn-id slot.
Encryption DES or 3DES. Troubleshooting steps and possible solutions are. Skeme provides anonymity repudiability and quick key refreshment.
IKE is the implementation of ISAKMP using the Oakley and Skeme key exchange techniques. Network Security 10 Final Exam Answers. ISAKMP defines payloads for exchanging key generation and authentication data.
And ISAKMP or Internet Security Association and Key Management Protocol is a protocol that is used to establish SA and cryptographic keys. Then what is the difference between IKE and ISAKMP protocol and how are they used in the IPSec protocol. This message is a general failure message meaning that a phase 1 ISAKMP request was sent to the peer firewall but there was no response.
ISAKMP également appelé IKE Internet Key Exchange est le protocole de négociation qui permet à deux hôtes de saccorder sur la manière de construire une association de sécurité IPsec. XXX - Add example decoded traffic for this protocol here as plain text or Wireshark screenshot. The ISAKMP dissector is fully functional partially functional not existing.
These formats provide a consistent framework for transferring key and authentication data which is independent of the key generation technique encryption algorithm and authentication mechanism. Phase 1 creates the first tunnel which protects la ter ISAKMP negotiation messages. An encryption method.
Whatever the current state is. RFC 2408 ISAKMP November 1998 communications depends on the individual network configurations and environments. Implementations MAY additionally support ISAKMP over other transport protocols or over IP itself.

Isakmp Ike Phase 1 Status Messages Mm Wait Msg Tunnelsup
Internet Security Association And Key Management Protocol Isakmp

The Difference Between Ike And Isakmp Protocol The Security Buddy

Internet Security Association And Key Management Protocol Isakmp The Ims Ip Multimedia Concepts And Services Second Edition Book

1 Placement Of Isakmp In The Network Architecture Standard Ipsec Download Scientific Diagram
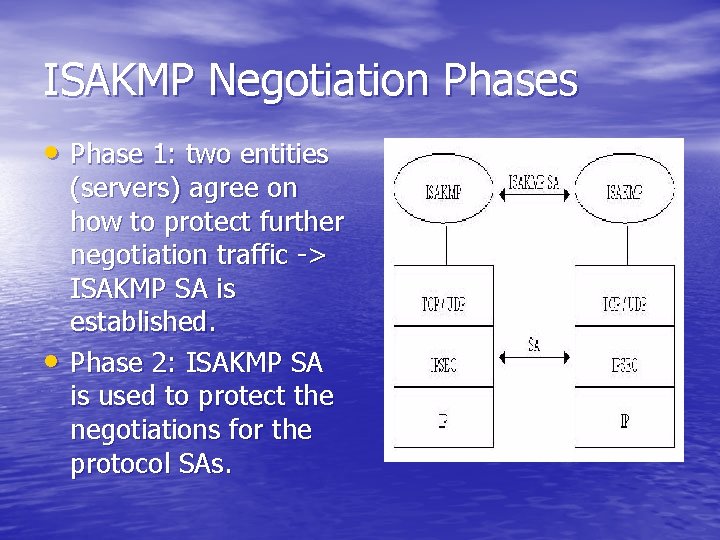
Isakmp Presented By Gary Aoki Linan Chang Thu

Gdoi Phase 1 Authentication Based On Isakmp Exchanges The Indicates Download Scientific Diagram
How To Analyze Ipsec Failures Huawei Firewall How To Analyze Ipsec Failures Huawei
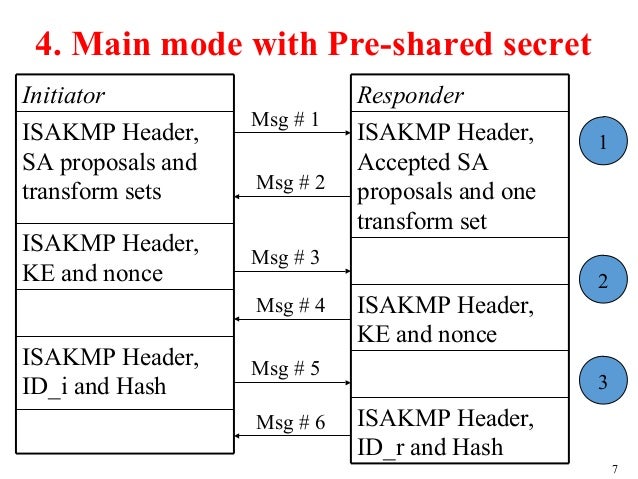
Internet Security Association And Key Management Protocol Isakmp

Isakmp Ikev1 Protocol Overview Wireshark Analysis Youtube

Deploying An Ipsec Secure Channel Isakmp Sa Empty Network Engineering Stack Exchange

Isakmp Sa Negotiation In Aggressive Mode Download Scientific Diagram

Isakmp Sa Negotiation In Aggressive Mode Download Scientific Diagram

Ipsec Ike Phase 1 Isakmp English Youtube
Internet Security Association And Key Management Protocol Isakmp Overview Ipv6 And Ip Security